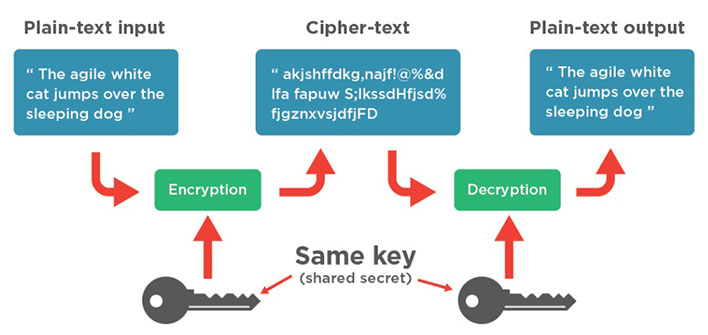
Encryption is the process of encoding information. It is vital for protecting confidential information and expediting compliance with PCI-DSS, GDPR, HIPAA, SOX, other government regulations and state privacy laws.
Restricting access is sometimes sufficient, but encryption is always strongest.
Use Field Encryption used to...
Protect sensitive data:
Segregate the way data is displayed:
Field Encryption supports a single Key Manager / single Token Manager for multiple Data Managers
The Field Encryption solution allows you to fully protect all sensitive data without modifying your software. A change that is done externally without changing the Level-Check of your file (i.e. Files remain intact), but is reflected in:
IBM i 7.1 introduced the database exit program FIELDPROC. Using this feature for encryption makes it part of the database capabilities and eliminates use of additional files. Field Encryption was designed after the FIELDPROC announcement and does not need to have backward capability with outdated technology – providing efficiency and simplicity.
Files are never locked; they are available for application use even when encryption keys are refreshed.
Supports all types of data: Character, Zoned Decimal, Packed Decimal, CLOB and BLOB. Supports null-capable data as well as non-null-capable data.
Comprehensive Find Sensitive Fields system provides superior quality in searching based on iterations over partial estimation of size, type, name, text, etc.
Works on a wrapper program, so does not require the program source.
Optimized for data masking and consumes no CPU for decryption in such cases.
KEK (Key encrypting Keys) as well as Data Keys can be automatically changed, unattended.
In a multi-site environment, a single key manager can be set to support all sites, centralizing all key-related activity.
Key Manager, Data Manager, and Token Manager can optionally be installed on different IBM i LPARs.
Supports both Encryption and Tokenization.
Policy driven security and limitation of capabilities ensures Separation of Duties.
Comprehensive logs for tracing of activities.
Full journaling system guarantees that any change in parameters is logged.
Uses NIST encryption standards.
Adheres to both GDPR, PCI and COBIT standards.
128-bit, 192-bit, and 256-bit AES encryption supported.
Based on IBM Native APIs.
Our field encryption solution is powered by the IBM i's native cryptographic services which complies with Advanced Encryption Standards (AES).
Even AES 128 is considered by NAS as suitable to encrypt “top secret” documents
For example... For a file with a record length of 200 bytes of which 2 fields of 10 bytes should be encrypted, the record length will be (if the field is a Key, the length is further increased):
SEE ALSO...