
The performance, reliability, and security of any software, from the simplest mobile application to complex enterprise platforms like JD Edwards, depends on the environment in which they operate. A full understanding of the software’s technical ecosystem is essential for maximizing uptime, optimizing performance, and protecting critical business data.
In the case of JD Edwards running on IBM i, this means expanding the administrator’s perspective to include not just JDE application security, but also the complexities of securing the IBM i operating system, and the policies & procedures that govern it.
In today’s environment, potential security threats can come in a multitude of ways – from people, places, and things -- which requires a periodic re-evaluation of your application security strategy.
How long has it been since your security strategy was designed & implemented? Has your business grown, or have your processes changed since your last holistic evaluation?
Most application analysts are acutely aware that good security control is much more complex than maintaining the on/off switches! Beyond the common best practices, additional risks are presented by:
Each of the above risks may allow unintended circumvention of your application controls, so it is also essential to investigate potential mitigations such as:
Security threats continue to creatively evolve. Your application security strategy should as well! Take the time to dig into the people, places, and things in your environment to assess and fortify your application security strategy.
JDE business logic and user security is contained within the JD Edwards application. The application then connects to a database. We need to think about what happens if/when users connect to the database without using the JD Edwards application. Users who connect this way aren’t subject to JD Edwards security or audit controls.
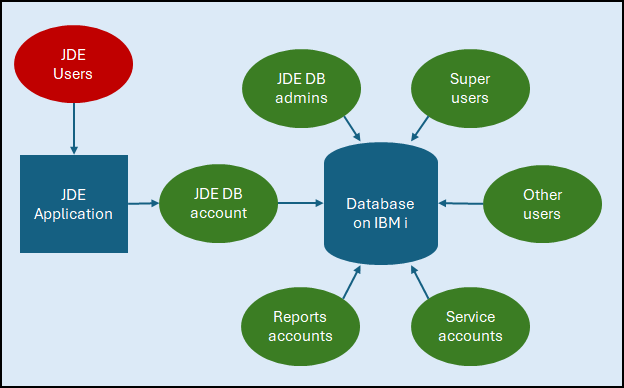
All the profiles in green are connecting without the protection of JDE security.
JD Edwards database and service accounts are IBM i user profiles that can also be used for FTP, TELNET, ODBC, file browsing and more. If someone knows the password then these profiles can be used as if they are regular users on the server. It is essential to put limits around what these profiles can do.
Four strategies to protect JD Edwards data on IBM i:

Now with the first two layers taken care of, let’s now consider Layer 3.
We also need to think about the system itself on which the database resides because we want to do everything possible to keep JD Edwards running reliably in all situations.
Four strategies for JD Edwards availability on IBM i:
There’s plenty to think about! Keep in mind, the average time it takes to detect a data breach is not measured in days, but in weeks and months. Once detected, containment can take almost as long as initial detection -- all the while leaving your data at risk. These breaches can create losses in productivity, competitive advantage, costs associated with the response effort, specific financial losses such as fines and judgements, and have the potential to significantly damage brand reputation and future revenue.
Please feel free to reach out, we are here to help and advise with your JD Edwards on IBM i security considerations.Protect your JD Edwards data and IBM i system with the experts at Kisco Systems.
Contact us today to schedule a security assessment and take the first step towards peace of mind.
Melissa Webb, JD Edwards Application Security Specialist
mwebb@nuverge.com
www.nuverge.com/securityaudit
Justin Loeber, Head of Business Development
justin@kisco.com
www.kisco.com
Kisco Systems is your trusted partner for IBM i security software and services, offering solutions for system monitoring, data protection, and audit. Together with our partners, we provide top-to-bottom security solutions for IBM i.
1PM EST, March 21 2024